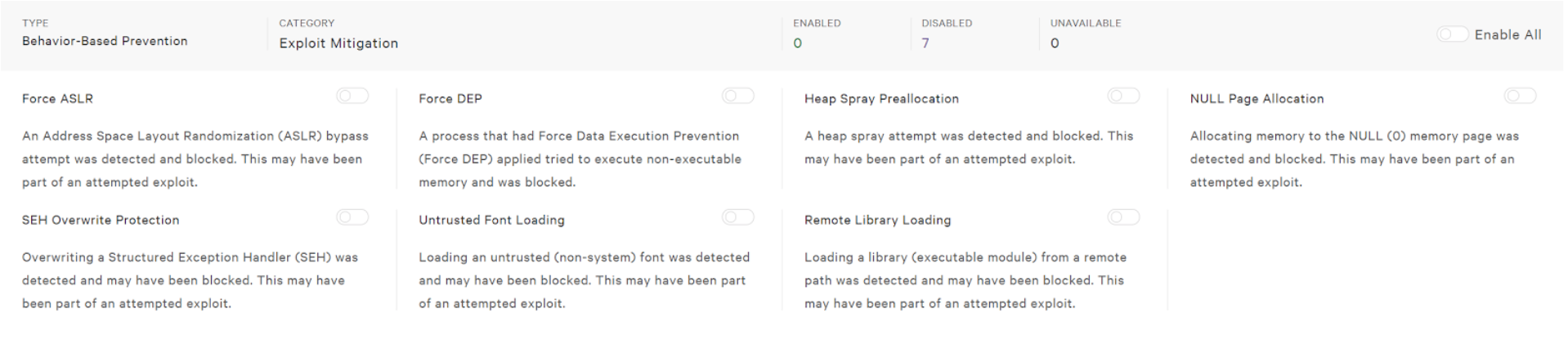
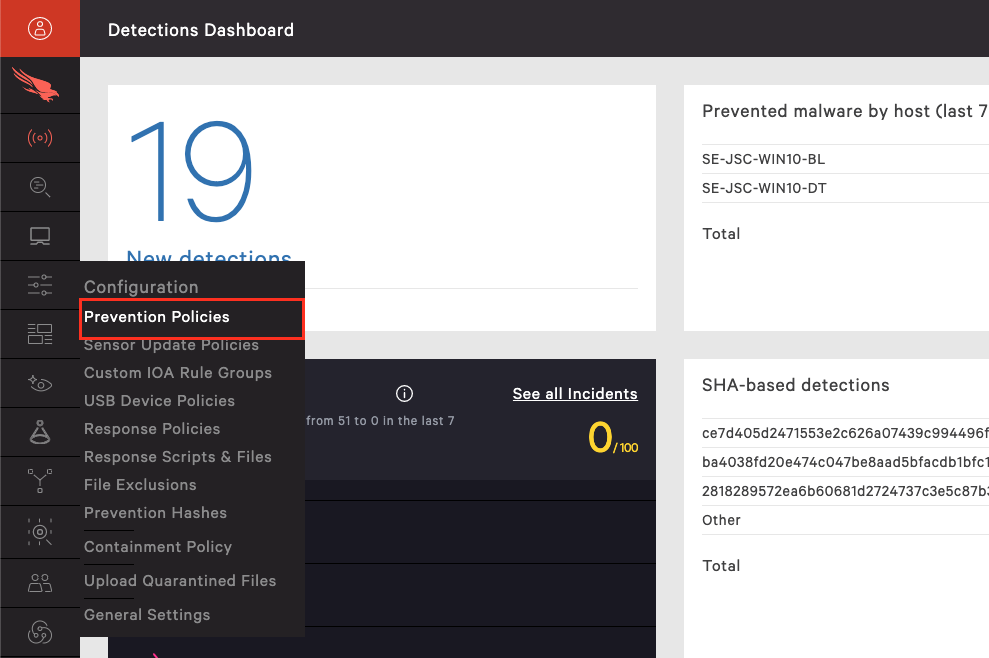
CrowdStrike Operational Best Practices - Groups Sensor Deployments and Prevention Policies II | PDF | Antivirus Software | Ransomware

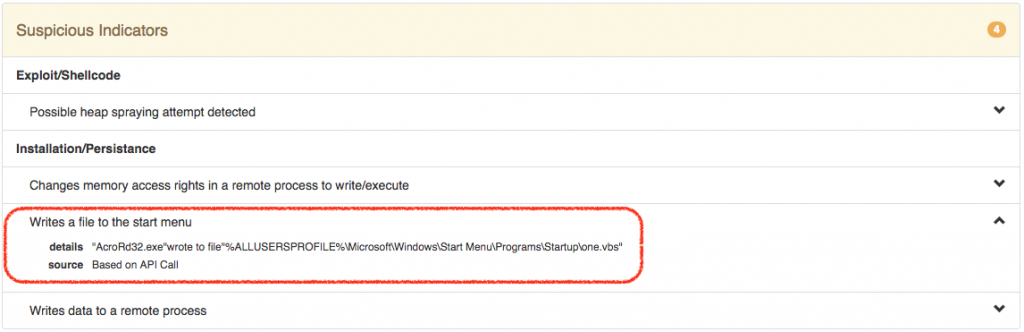
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for '40_John+Titmus-CrowdStrike'

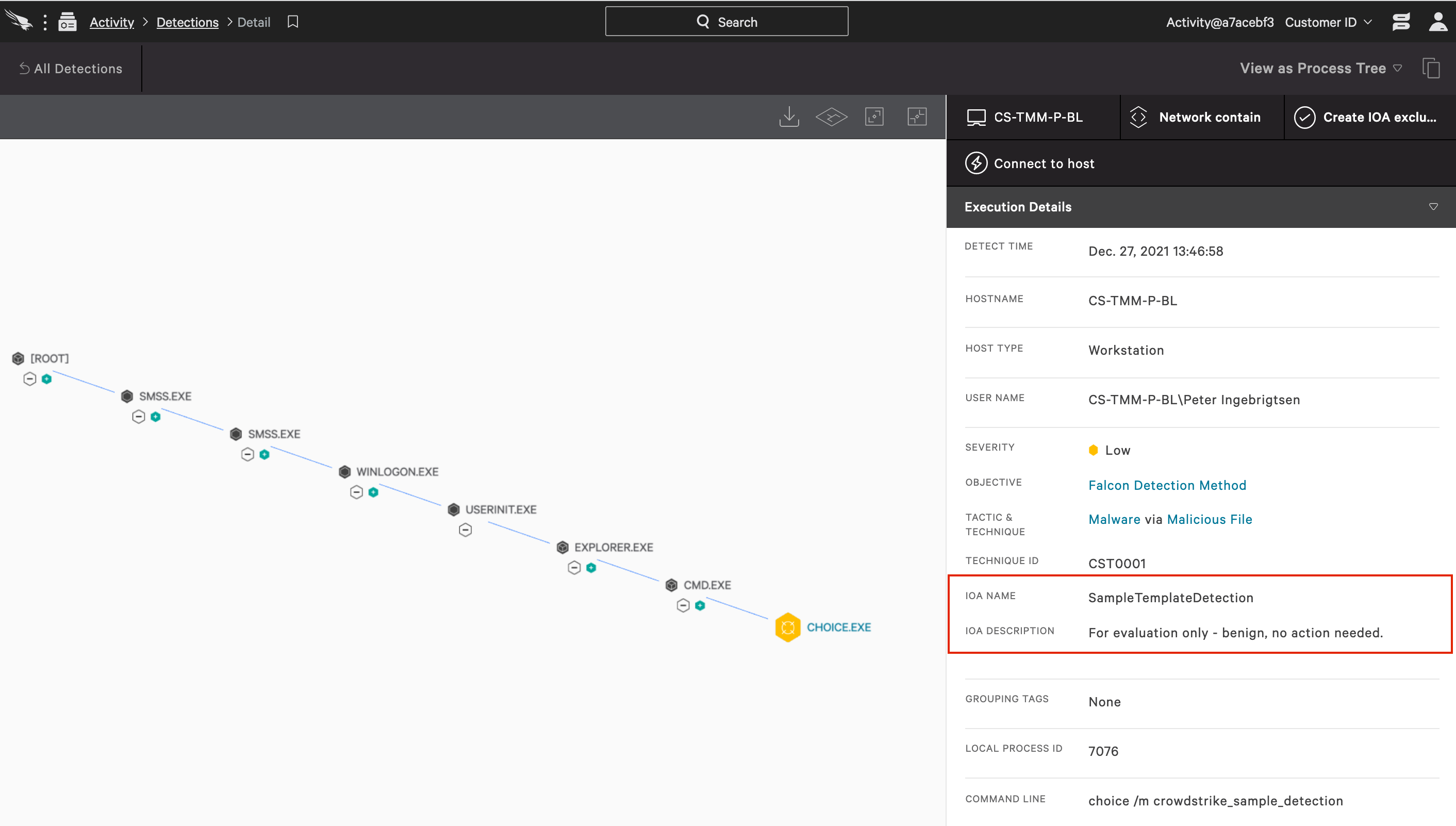
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'https://falcon.crowdstrike .com/activity/detections/detail/a5620d817603425f6809b58e28709d4a/1168231932540?processView=tree'