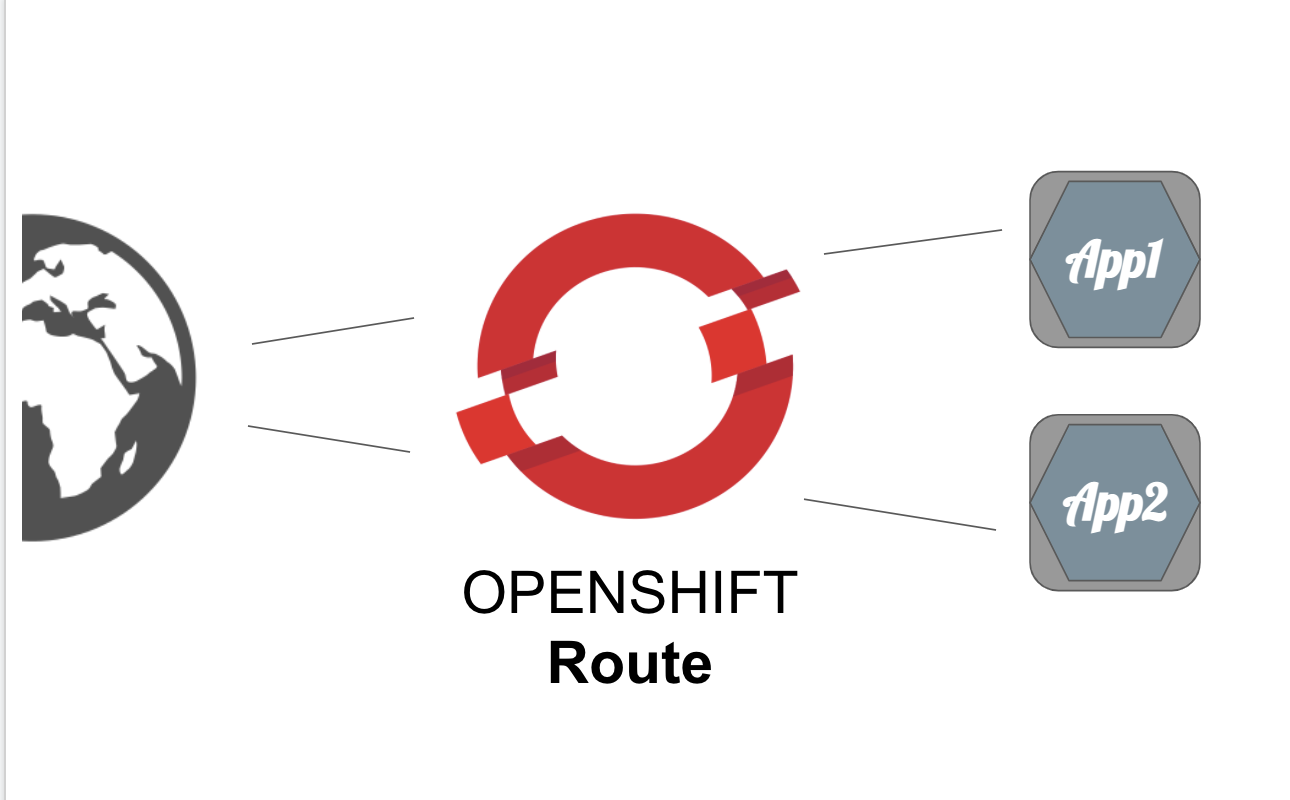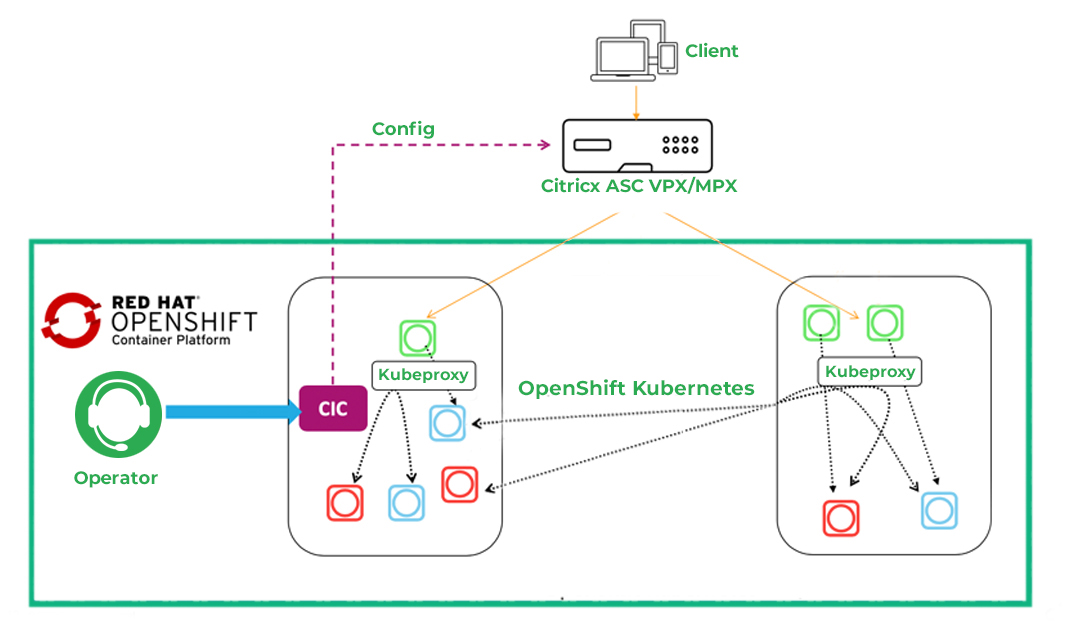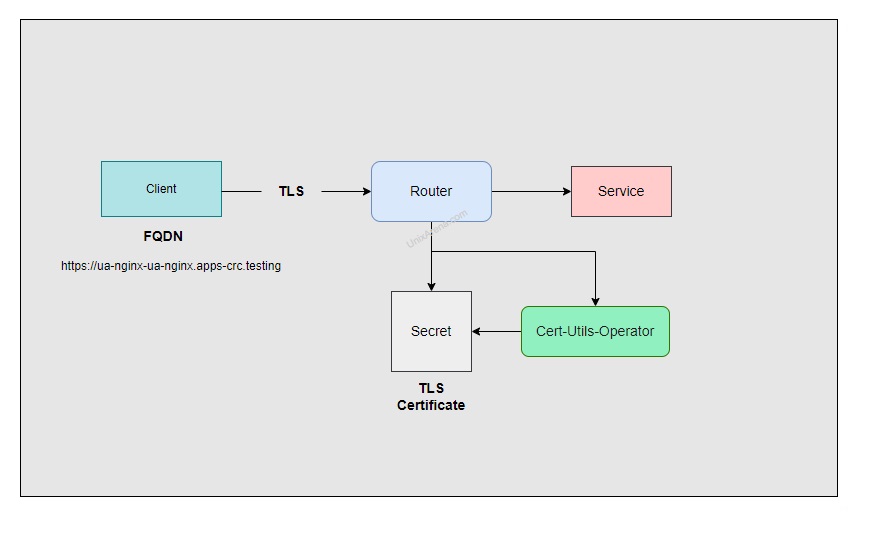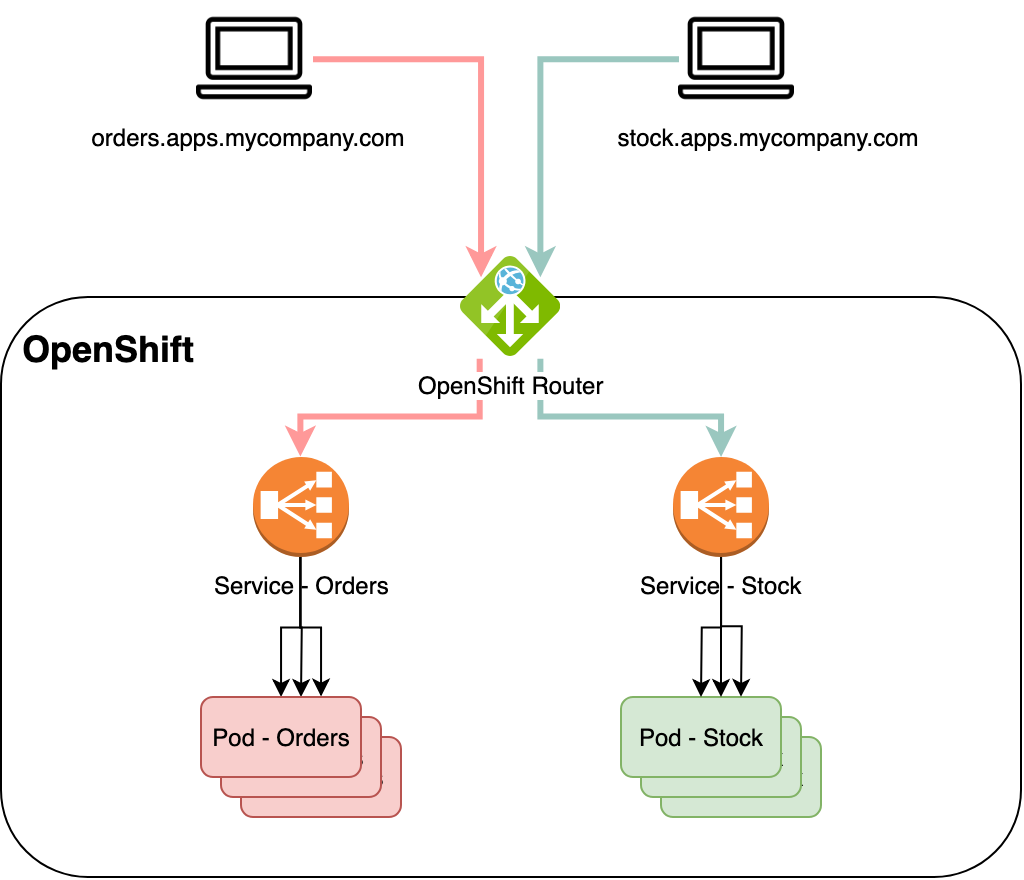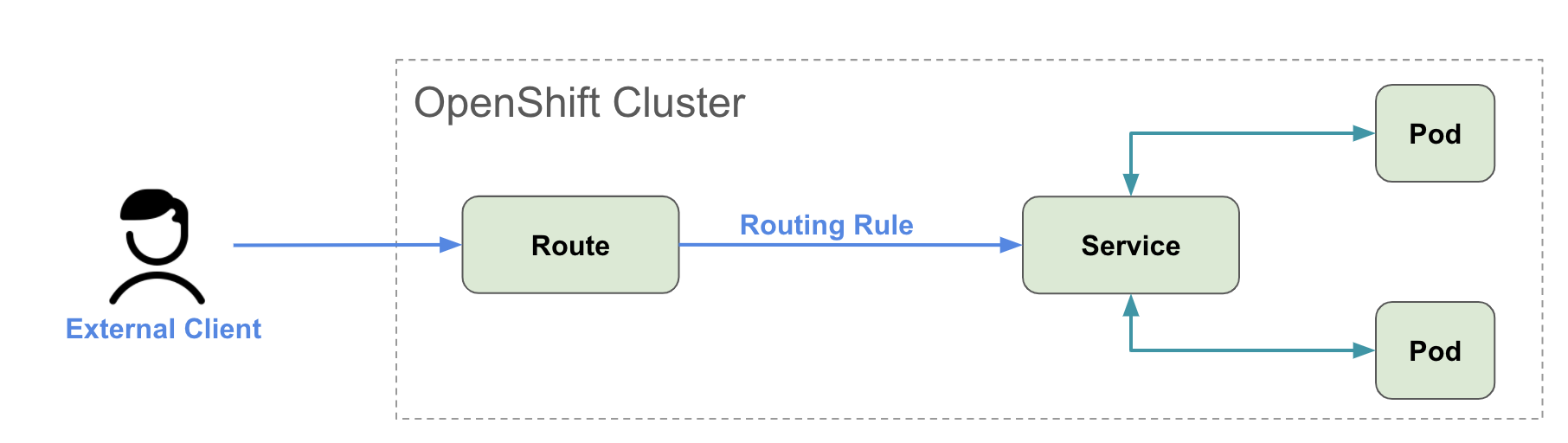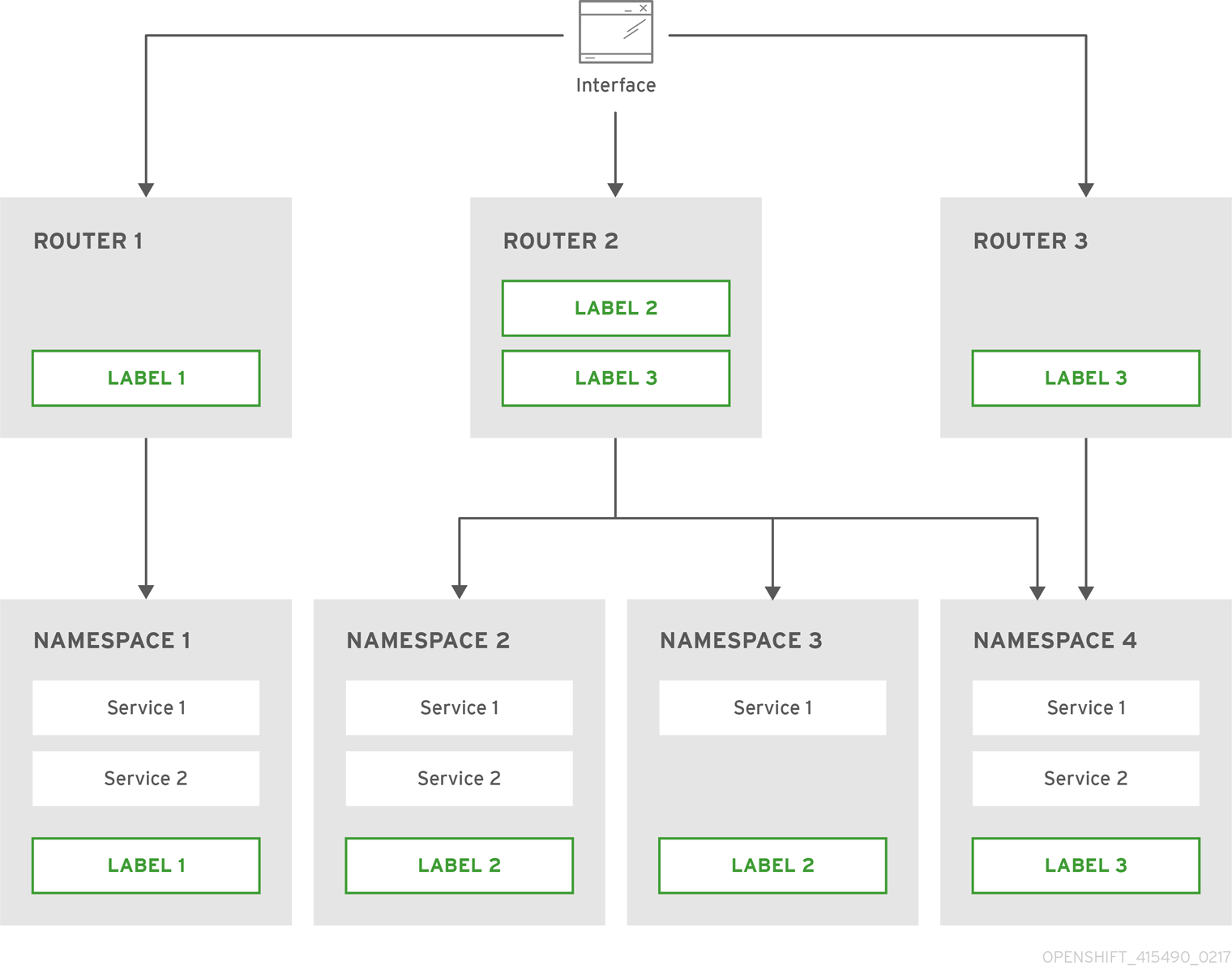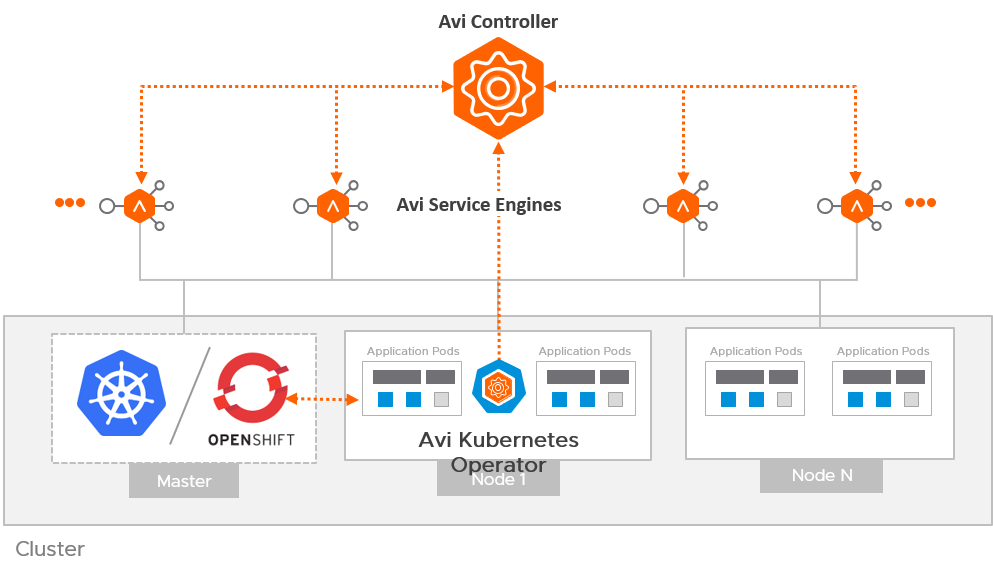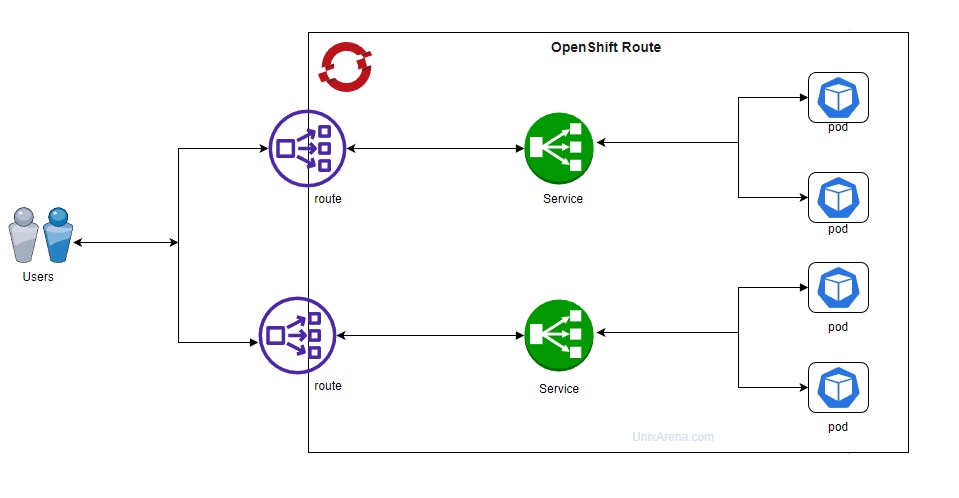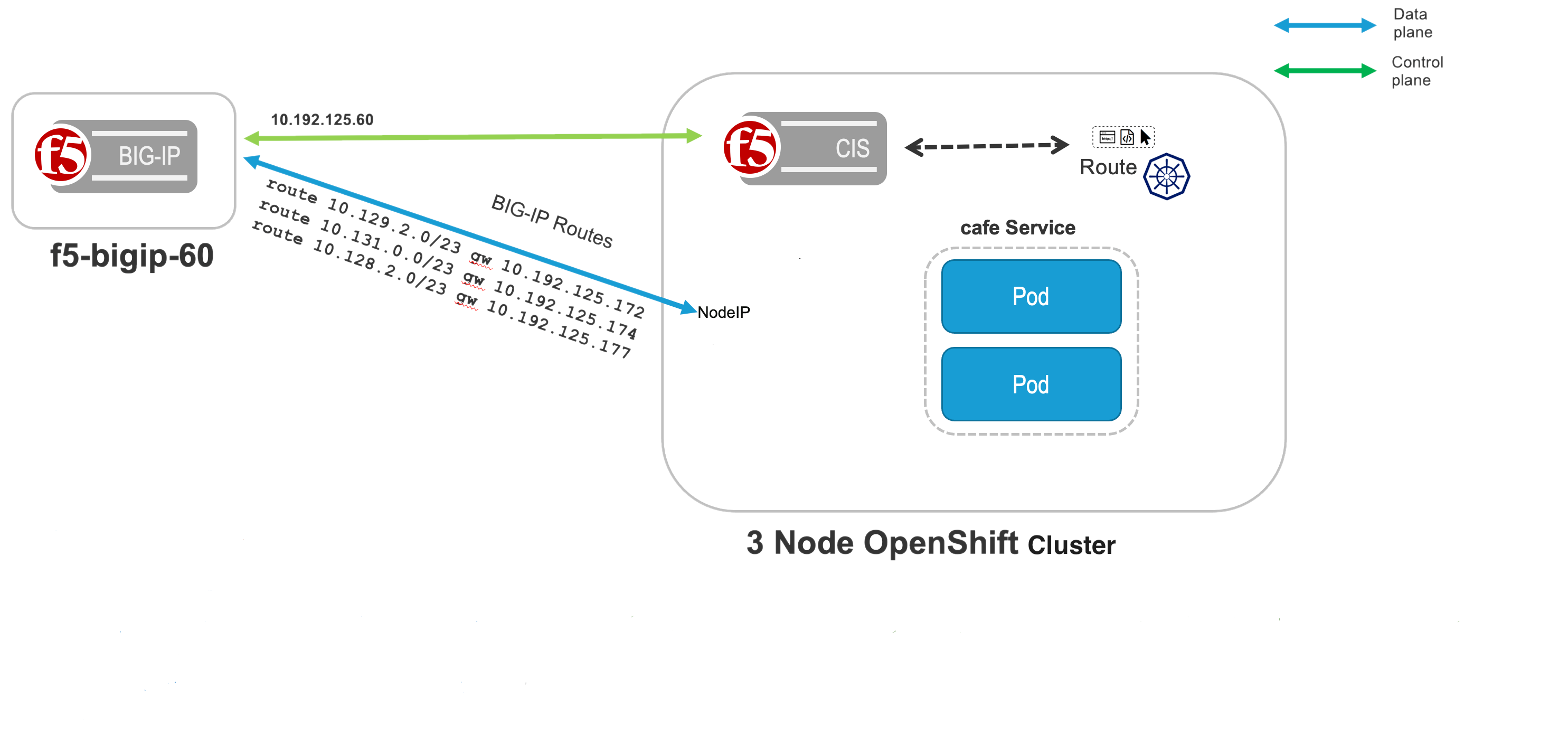
OpenShift 4.12 and F5 BIG-IP Container Ingress Services (CIS) User-Guide for Standalone BIG-IP using OVN-Kubernetes iCNI with NO Tunnels
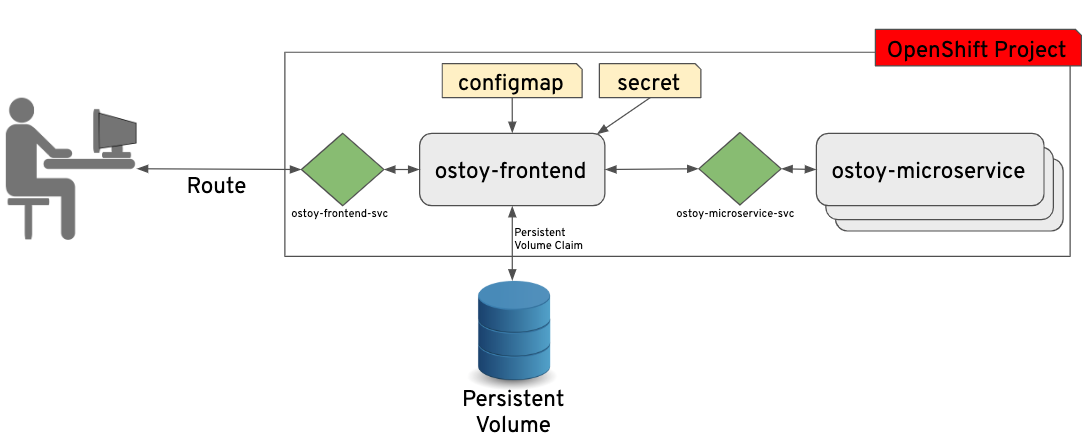
How to network within Red Hat OpenShift Service on AWS clusters | How to deploy an application using Red Hat OpenShift Service on AWS | Red Hat Developer
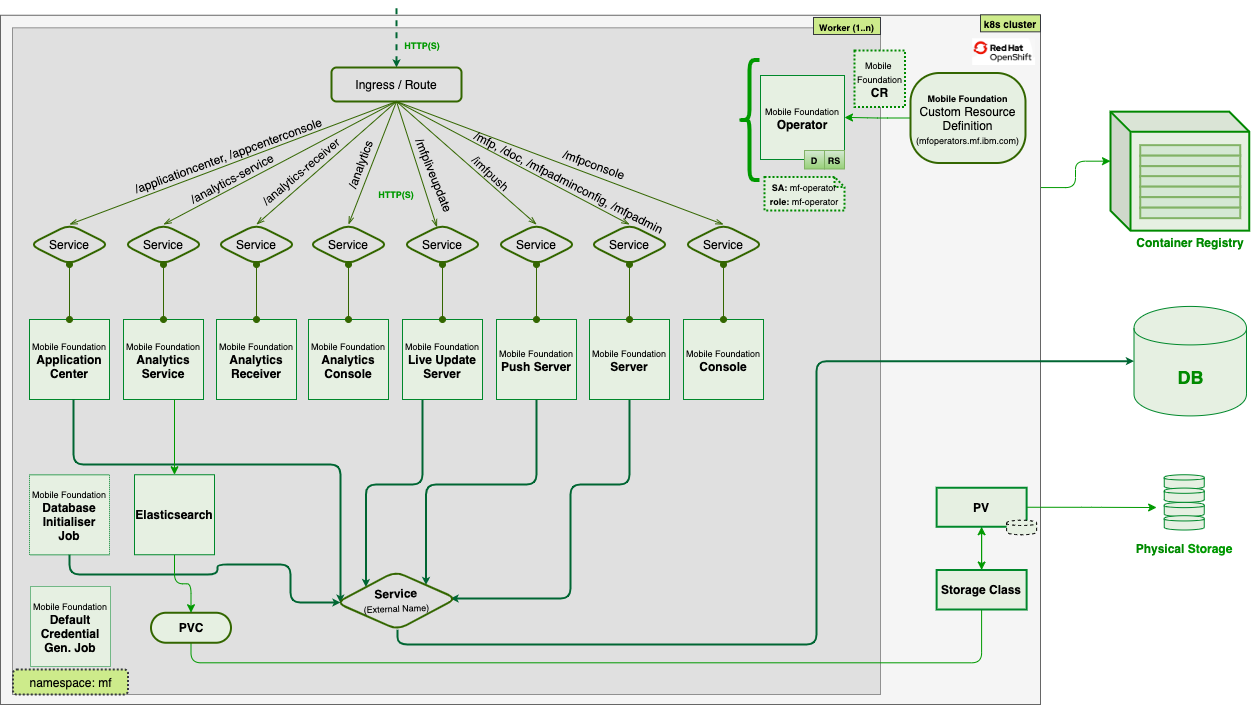
Deploy Mobile Foundation to an existing Red Hat OpenShift Container Platform - IBM Mobile Foundation Developer Center