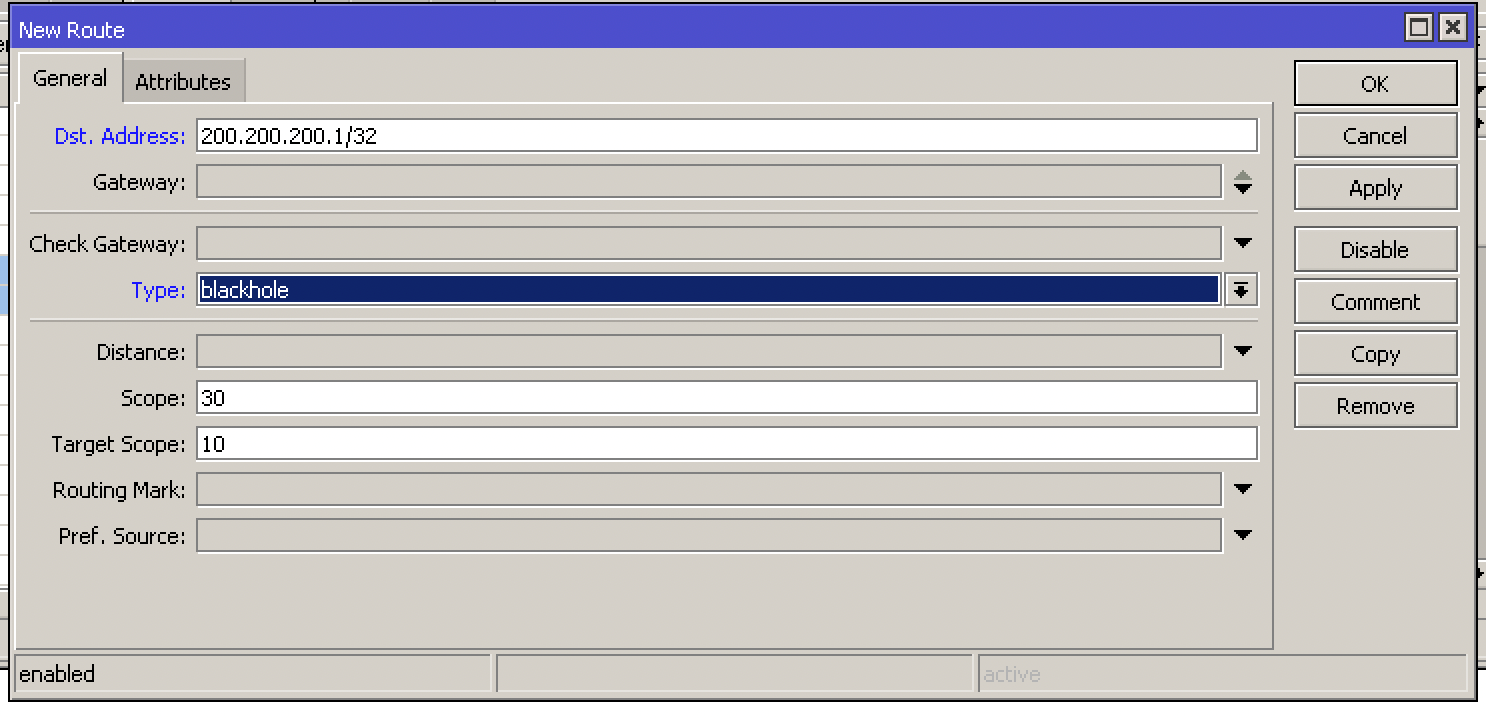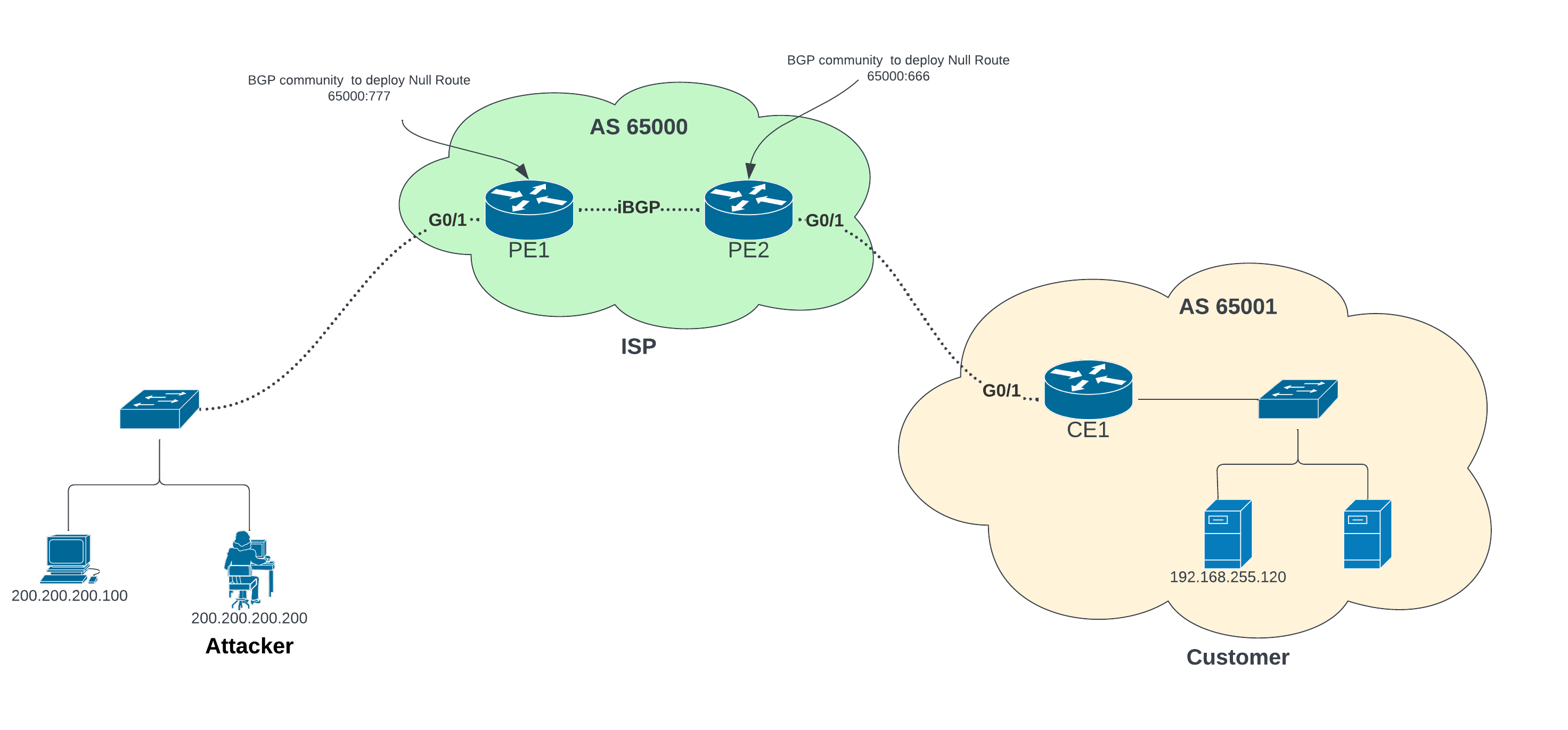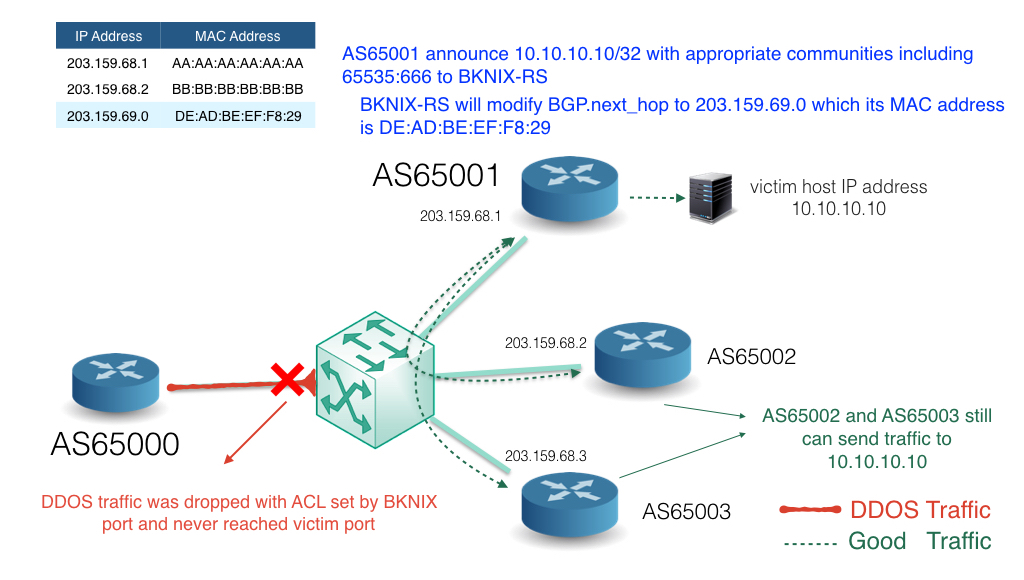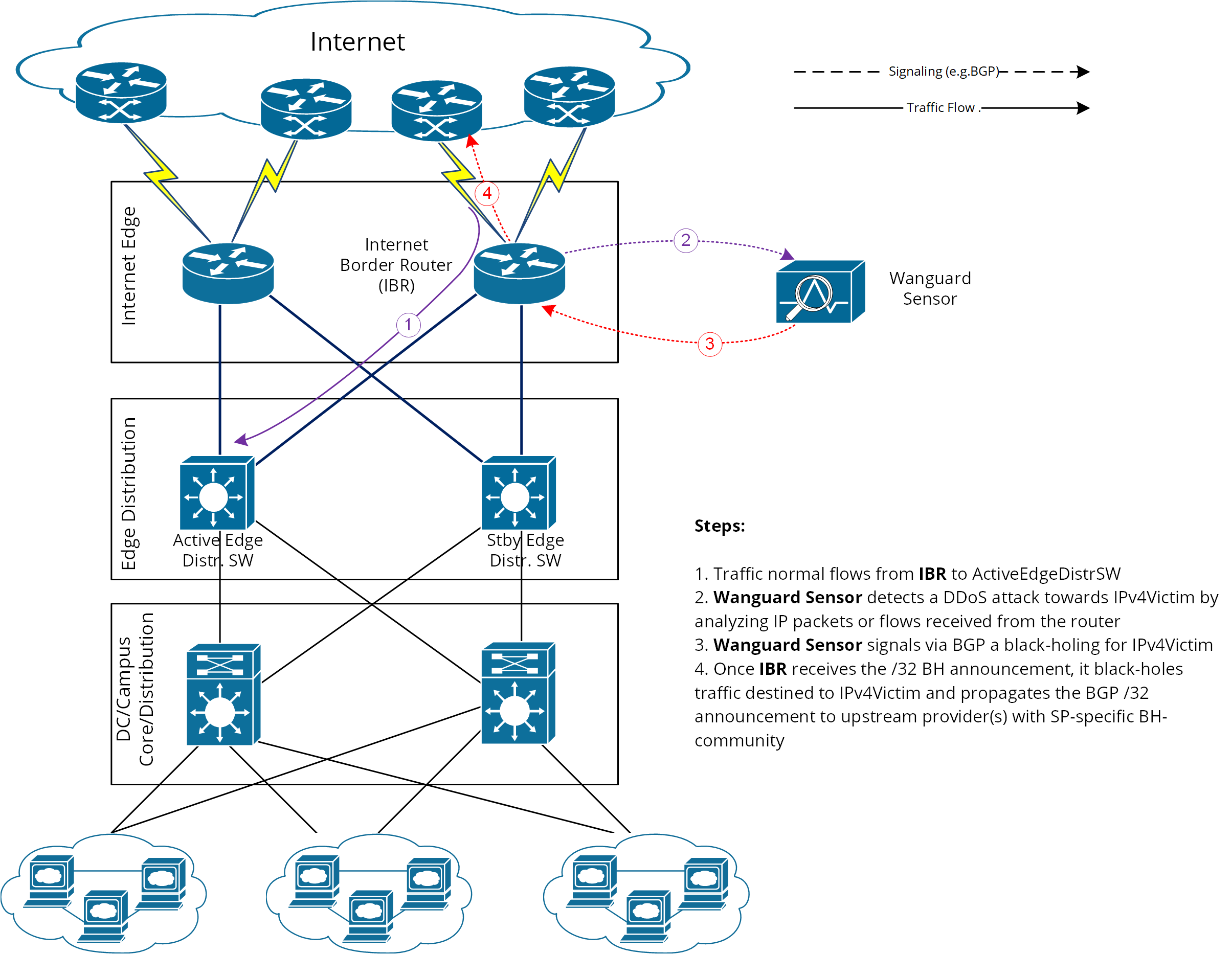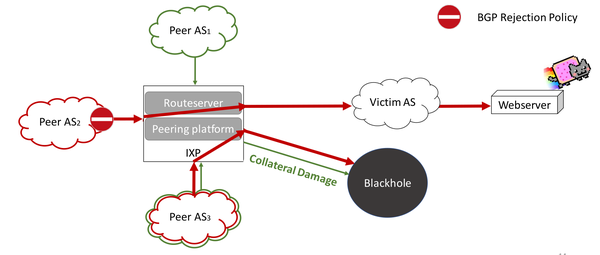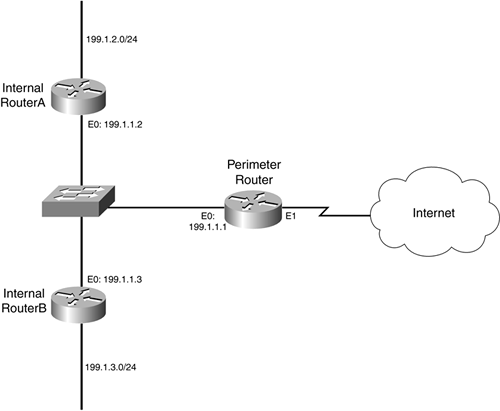
Static and Black Hole Routing :: Chapter 15. Routing Protocol Protection :: Part VI: Managing Access Through Routers :: Router firewall security :: Networking :: eTutorials.org

Mitigation of black hole attacks in Routing Protocol for Low Power and Lossy Networks - Ahmed - 2016 - Security and Communication Networks - Wiley Online Library